Hi.
I have emailed the support box twice about this but not received any reply whatsoever. Posting here for visibility. The issue persists and now when the device waters while offline it doesn’t show properly in the calendar (although it does appear in history).
I’m having issues with my Rachio Gen3 sporadically not picking up an IP address from the DHCP server. This manifests as the controller going offline for extended periods of time. Sometimes the only way to bring it back is to power cycle it and maybe the WiFi AP as well.
Very similar to the problem experienced by this user:
DHCP Logs from Router:
17:52:04.236812 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:52:05.238235 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:52:52.425803 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:52:52.426611 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:52:57.425302 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:52:57.426086 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:53:05.425515 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:53:05.426320 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:53:19.027327 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:53:19.028084 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:53:23.021558 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:53:23.022348 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:53:32.027259 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:53:32.027983 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:54:21.015560 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:54:21.016414 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:55:26.008931 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:55:27.010392 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:10.162058 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:10.162816 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:15.155670 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:15.156381 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:23.154885 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:23.155615 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:36.317638 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:36.318363 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:40.314144 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:40.314956 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:56:49.314132 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:56:49.315043 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:57:05.311458 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:57:05.312279 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:57:37.312160 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:57:37.312941 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:58:41.301388 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:58:42.302848 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:59:26.905857 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:59:26.906590 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
17:59:26.909426 IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 58:d5:0a:bd:27:b0, length 300
17:59:26.910153 IP 192.168.99.1.67 > 255.255.255.255.68: BOOTP/DHCP, Reply, length 300
*No further requests after this point. Controller came back online but had been offline on/off sporadically for several days.
You can see that in the period of a very short space of time the device requested a DHCP address multiple times, and the router sent responses.
Also attached -
-
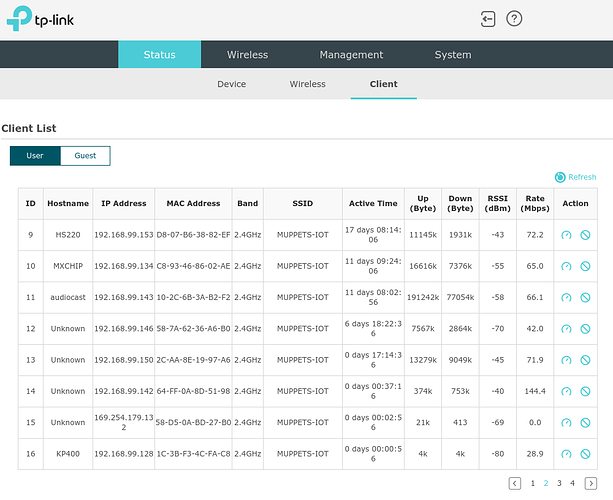
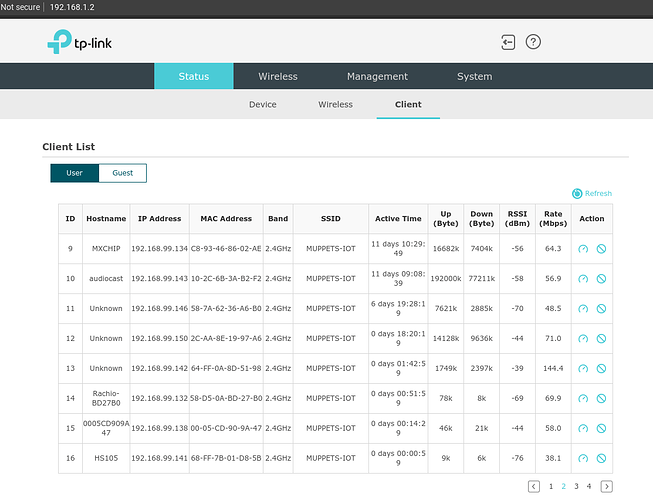
Screenshots of WiFi AP page showing that the Rachio is connected to the AP, but is not accepting an IP and therefore taking a 169.254.x.x IP address. This also shows that the signal strength is -69dB, which is plenty strong enough for a reliable connection. The controller is close to a garage door opener device which does not have any of the same connectivity issues.
-
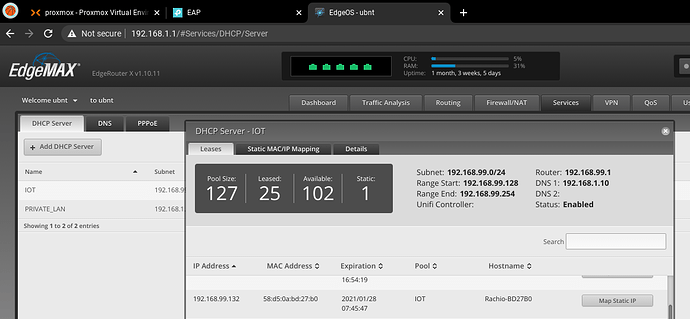
Screenshot from router showing the DHCP address leased to the device (should it decide to accept it); and
-
Another screenshot from the AP a short while later this morning, when the device finally accepted the IP and came back online.
Any advice you can offer would be appreciated. Let me know if you’d like me to run any tests on my end or grant you access to logs etc.