Apple HomeKit, iOS/iPadOS, and the Rachio 3
(And other networking notes)
There are some misunderstandings about the relationships between Apple HomeKit, HomeKit accessories, and iOS/iPadOS (hereinafter simply “iOS”).
An iOS device need only be present and active for the purpose of adding an accessory to HomeKit. And, of course, personal interaction with HomeKit. Thereinafter, HomeKit communicates back-and-forth with the accessory without the need for an iOS device being present. It has to be that way, otherwise how would HomeKit Automation work?
Crude “ASCII art” drawing of the relationship:
iOS device(s) <-> HomeKit <-> accessories
Furthermore: All documentation says “on the same WiFi network.” In reality they all need merely be on the same network, during setup–wired or wireless, 2.4Ghz or 5GHz wireless, not necessarily the exact same physical network. E.g.: I initially set up HomeKit to run on the Apple TV in our computer room. That ATV has an Ethernet connection. So, too, does our Lutron Casèta Smart Bridge. All our other ATVs are on WiFi, as is our Ranchio 3 irrigation controller.
When I write “same network” I mean the same flat network. I.e.: No intervening routing, VLAN isolation, etc. Otherwise the network discovery protocol (protocols?) they need to remain aware of one another won’t work, because those protocols don’t cross routed boundaries or VLANs. (See also notes about “mesh WiFi,” below.)
Here’s a neat thing: If you have multiple HomeKit-capable hosts on that flat network (multiple ATVs, HomePods): If the one serving as HomeKit controller goes off-line, another takes over for it.
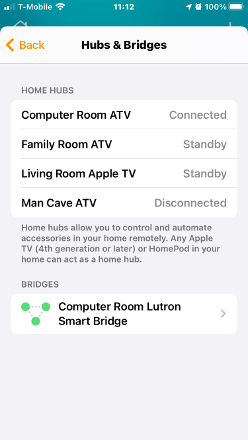
E.g.: Screen-shot of our HomeKit Hubs & Bridges:
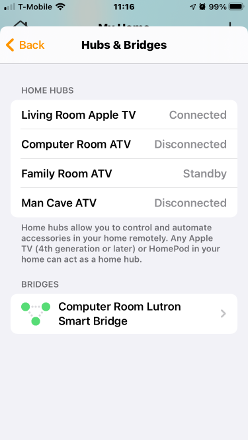
You’ll notice “Computer Room ATV” is connected, and the others are on standby or disconnected. Now I unplug the Computer Room ATV:
Now “Family Room ATV” is running the show.
For those who may be wondering: Yes, our Rachio 3 remained connected to HomeKit through this–I turned a zone on/off from my iPhone.
Some Notes On WiFi Networking
(and mesh networks, in particular–some copied from an earlier post of mine)
Here are things I’ve seen cause problems with WiFi networks:
- Poor WiFi router/access point equipment–particularly “all-in-one” routers/switches/APs
- Poor WiFi router/access point siting (e.g.: WiFi router/AP located in one corner of a structure)
- WiFi repeaters (aka: “range extenders”)
- WiFi mesh products (often little more than WiFi repeaters with dubious “smarts”–more detail below)
- WiFi routers/APs with client isolation enabled
- WiFi routers/APs with band steering enabled–particularly in multi-router/-AP installations
- WiFi routers/APs that are placed too-closely to one another, creating overlapping coverage, resulting in devices “flapping” between them
I’ve often seen WiFi mesh networks, in particular, to be the culprit in problems with devices that are meant to maintain persistent connectivity, because they often have designed-in “smarts” meant to transparently “improve” network performance. Unfortunately, sometimes those “smarts” aren’t so smart, because they block network service announcement or discovery protocols such devices need to work. (E.g.: MDNS/Bonjour.) Sometimes you can’t turn those “smarts” off.
Even worse: I witnessed one WiFi mesh network product that would allow network service advertising/discovery protocols, then later decide to filter them out as “unnecessary noise.” This resulted in devices working, then, later, mysteriously failing. (Even worse yet: This behavior was not documented and the product’s own tech support people were not aware of it. It was discovered via network traffic analysis.)
(WiFi mesh products aren’t necessarily the only guilty parties. I’ve seen incidences of other WiFi routers and APs that do the same thing–though usually you can turn that stuff off in those.)
That’s all I can think of at the moment. I’ll update this post, as necessary, as long as the forum software will allow me, following which I’ll add updates as additional posts.,